Penetration Testing
How it works
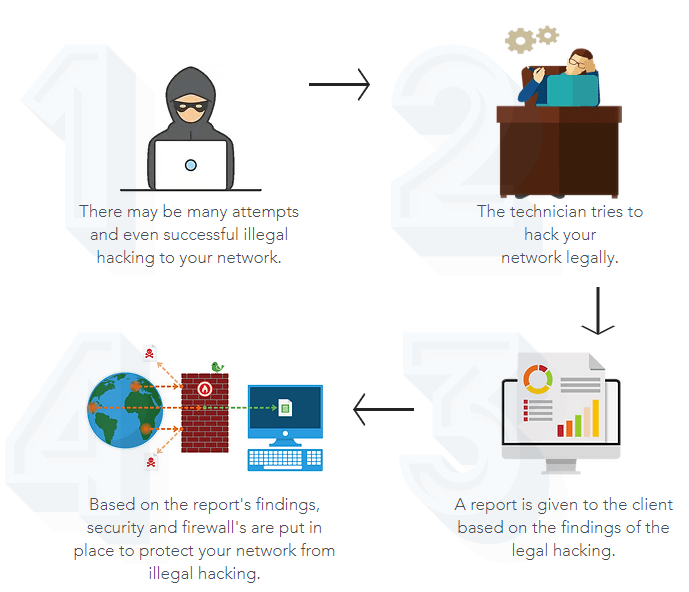
What is Penetration Testing?
Penetration testing is an authorized, benign attack of your online system, a simulation of a real-world attack from both external and internal threats. Knowing the limits of your network security is vital to understanding and mitigating your vulnerabilities. Malicious attackers could strike at any time and the impact of losing sensitive customer data or experiencing system downtime has serious consequences.
The need for providing secure websites and web applications has never been more important than it is right now. Attackers are always on the prowl to expose vulnerabilities in content that is publicly available online. The number of ways in which applications can interface with one another is increasing, and web application developers are delivering increasingly sophisticated approaches for presenting data to users. The increasing levels of functionality has provided business with huge opportunities for innovation. However, the potential vulnerabilities that can be introduced are also growing at an alarming rate. Businesses and organizations need to understand this and incorporate security in their approach to providing this functionality.
Our Approach
We follow a structured approach to penetration testing using PCI DSS as our guide. We provide a detailed document with the results of the scans, categorizing the threats into low, medium and high-risk threats. We also provide guidance on the remediation steps.
Our recommendation is that a penetration test is performed on an internet-facing website or internal network, at least every 6 months or after a major change has been implemented.
Ethical Hacking
The term “white hat” in Internet slang refers to an ethical computer hacker, or a computer security expert, who specializes in penetration testing and in other testing methodologies that ensures the security of an organization’s information systems.
